Desktop PCs can always be reimaged. It’s a pain, but downtime only affects one person. Servers, on the other hand, need to be up the vast majority of the time. Rebuilding servers affects lots of people, often in mission-critical ways. While most servers don’t spend much time browsing the web or receiving emails, some have quite a bit of exposure.
While every Windows server obviously needs anti-malware protection, terminal servers and others providing virtual desktops or remote access could clearly benefit from the real-time protection promised by Microsoft’s Morro project (now officially known as Microsoft Security Essentials). There are those, in fact, who see it as Microsoft’s responsibility to provide malware protection for all of its products, given their penchant for attracting malicious code.
Unfortunately, MSE is only available for Windows XP, Vista, and 7. No mention of servers. No Googling suggested that server support is in the pipeline. While Clamwin does a perfectly adequate job protecting servers, full-blown server anti-malware solutions aren’t cheap and, again, lack MSE’s near real-time updates.
Then again, would you entrust your mission critical servers to a Microsoft anti-malware solution? Take the survey and talk back below.
Should Microsoft provide a server anti-malware solution?
* Yes! I need to save the money and I want the real-time updates
* Yes they should, but I'd still use a 3rd-party solution
* No, Morro should stay consumer-oriented; I want a robust solution
* Who cares? That's what Clamwin is for
Source: zdnet
Monday, June 29, 2009
Monday, June 22, 2009
Microsoft patches WebDAV security vulnerability in bevy of updates
Microsoft patched a WebDAV security vulnerability in Microsoft Internet Information Services (IIS) Web server as part of its monthly Patch Tuesday bulletin release. In all, the software giant issued 10 bulletins, six labeled critical in a mammoth release of security fixes addressing 31 vulnerabilities.
Microsoft acknowledged the IIS Web server flaw last month after the U.S. Computer Emergency Response Team warned of publicly available exploit code and active exploitation of the vulnerability. MS09-020 patches a remote authentication bypass vulnerability in the IIS WebDAV extension, a collection of tools used to publish content to IIS Web servers. The WebDAV vulnerability, which was discovered by security researchers at Palo Alto Networks, is due to the lack of proper checks on the URL in a WebDAV request, leading to a bypass on IIS directories. Microsoft IIS versions 5.0-6.0 are affected. The update is rated important. If successfully exploited, it could give an attacker elevated privileges to gain access to sensitive data.
Source: searchsecurity.techtarget.com/news/article/0,289142,sid14_gci1358796,00.html
Microsoft acknowledged the IIS Web server flaw last month after the U.S. Computer Emergency Response Team warned of publicly available exploit code and active exploitation of the vulnerability. MS09-020 patches a remote authentication bypass vulnerability in the IIS WebDAV extension, a collection of tools used to publish content to IIS Web servers. The WebDAV vulnerability, which was discovered by security researchers at Palo Alto Networks, is due to the lack of proper checks on the URL in a WebDAV request, leading to a bypass on IIS directories. Microsoft IIS versions 5.0-6.0 are affected. The update is rated important. If successfully exploited, it could give an attacker elevated privileges to gain access to sensitive data.
Researchers at security vendor Core Security Technologies discovered one of the IE flaws in October 2008. A security zone bypass vulnerability allows a website to perform actions, such as executing code, despite being disabled by the security level of a given Security Zone.
"In this case this is a variation of a previous bug, but this is a very important one," said Ivan Arce, chief technology officer of Core Security. "This is important enough to require people to address it quickly."
Other Microsoft Bulletins:
|
Source: searchsecurity.techtarget.com/news/article/0,289142,sid14_gci1358796,00.html
Sunday, June 14, 2009
Cloud computing security to grow in 2009
While enterprise users continue to spend a large percentage of their workday involved with messaging activities, the Internet remains a dangerous place for users. Websense, for example, reported that 57 percent of attacks are delivered via the Web. Commtouch found that SPAM accounted for 72 percent of all email traversing the Internet in the first quarter of 2009.
At the same time, today’s economic climate favors cost-effective solutions. IT expects to spend significantly less in 2009 than in 2008 on messaging. Nearly half (47 percent) of respondents expected IT spending to be lower in 2009 versus 18 percent who made similar projections last year.
As such, while server-based solutions will continue to dominate the messaging security market, cloud-based solutions will constitute a growing percentage of purchases. The number of respondents who deployed hosted security services grew by nine percentage points since last year. Over the next 12 months hosted anti-spam services, such as those offered by Kaspersky, Trend Micro and more recently Microsoft, are also expected to show their greatest growth.
Comprehensive security solutions will be particularly hot over the next 12 months. Although the vast majority of enterprises today deal with separate vendors for their various best-of-breed solutions, the number of respondents preferring a consolidated comprehensive centrally managed messaging security solution double while individual best of breed solutions dropped significantly.

At the same time, today’s economic climate favors cost-effective solutions. IT expects to spend significantly less in 2009 than in 2008 on messaging. Nearly half (47 percent) of respondents expected IT spending to be lower in 2009 versus 18 percent who made similar projections last year.
As such, while server-based solutions will continue to dominate the messaging security market, cloud-based solutions will constitute a growing percentage of purchases. The number of respondents who deployed hosted security services grew by nine percentage points since last year. Over the next 12 months hosted anti-spam services, such as those offered by Kaspersky, Trend Micro and more recently Microsoft, are also expected to show their greatest growth.
Comprehensive security solutions will be particularly hot over the next 12 months. Although the vast majority of enterprises today deal with separate vendors for their various best-of-breed solutions, the number of respondents preferring a consolidated comprehensive centrally managed messaging security solution double while individual best of breed solutions dropped significantly.

Labels:
Server Security,
windows server security
Sunday, June 7, 2009
Remote Server Monitoring Software - DreamSys Server Monitor
DreamSys Server Monitor, once a commercial remote server monitoring software, is now available as a free download from the developer’s homepage. The user still needs to enter registration information after installation. They are however available on the homepage without the need for registration or any other kind of data grabbing. The Server Monitor application can be used to monitor servers over a network or the Internet.
The system administrator starts by adding new servers that should be monitored to the application. Required information are a unique name, the server address and the monitoring type. Available monitoring types are TCP / IP, Ping or Services. Additional information might be required depending on the type selected. A TCP / IP monitoring for example requires a port that can be added in the same interface.

Three notification types are available. The administrator can be informed by email, message box or net message.
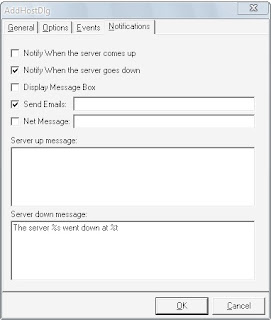
Specific parameters for every server can be configured in the Configuration View tab. It allows the user to change the monitoring interval, configure the connection timeout, set the mail server and enable the logging of events.

DreamSys Server Monitor can be used as a Internet or network monitoring software. It lacks some of the features of advanced monitoring applications that offer website or database monitoring but could be enough for administrators who do not need that functionality.
Source: ghacks.net/2009/06/06/remote-server-monitoring-software-dreamsys-server-monitor/
The system administrator starts by adding new servers that should be monitored to the application. Required information are a unique name, the server address and the monitoring type. Available monitoring types are TCP / IP, Ping or Services. Additional information might be required depending on the type selected. A TCP / IP monitoring for example requires a port that can be added in the same interface.

Three notification types are available. The administrator can be informed by email, message box or net message.

Specific parameters for every server can be configured in the Configuration View tab. It allows the user to change the monitoring interval, configure the connection timeout, set the mail server and enable the logging of events.

DreamSys Server Monitor can be used as a Internet or network monitoring software. It lacks some of the features of advanced monitoring applications that offer website or database monitoring but could be enough for administrators who do not need that functionality.
Source: ghacks.net/2009/06/06/remote-server-monitoring-software-dreamsys-server-monitor/
Monday, June 1, 2009
Forefront Security for Exchange Server SP1
Customers running Forefront Security for Exchange Server Service Pack 1 can now access a free tool from Microsoft designed to offer guidance on the factors capable of impacting their messaging servers. Adding security solutions to a server is a move that generally implies a tradeoff, as extra protection is, as a rule, synonymous with performance and throughput handicaps. The same is valid for Exchange Servers, but with the capacity planning tool, customers can take the necessary measures to compensate for the effects that the introduction of Forefront Security will have on their server infrastructure.
“The Forefront Security for Exchange Server capacity planning tool helps you understand what hardware, architecture, and configuration settings will produce recommended system performance and message throughput results for comprehensive protection of your Exchange Servers. The tool is an Excel spreadsheet with built-in workflow and can be used to help plan your Forefront Security for Exchange Server 10 SP1/SP2 deployment,” revealed Frank Trujillo, program manager, FSS.
Customers who are planning a deployment of Forefront Security for Exchange Server SP1 can turn to the capacity planning tool to fine tune the details of their implementation. But at the same time, the resource can be used to assess impact on existing deployments. According to Trujillo, a range of information is necessary in order to use the capacity planning tool, including server hardware and user load data for a specific Exchange Server environment.
For full info visit here: http://news.softpedia.com/news/Download-Forefront-Security-for-Exchange-Server-SP1-Capacity-Planning-Tool-112973.shtml
“The Forefront Security for Exchange Server capacity planning tool helps you understand what hardware, architecture, and configuration settings will produce recommended system performance and message throughput results for comprehensive protection of your Exchange Servers. The tool is an Excel spreadsheet with built-in workflow and can be used to help plan your Forefront Security for Exchange Server 10 SP1/SP2 deployment,” revealed Frank Trujillo, program manager, FSS.
Customers who are planning a deployment of Forefront Security for Exchange Server SP1 can turn to the capacity planning tool to fine tune the details of their implementation. But at the same time, the resource can be used to assess impact on existing deployments. According to Trujillo, a range of information is necessary in order to use the capacity planning tool, including server hardware and user load data for a specific Exchange Server environment.
For full info visit here: http://news.softpedia.com/news/Download-Forefront-Security-for-Exchange-Server-SP1-Capacity-Planning-Tool-112973.shtml
Subscribe to:
Posts (Atom)

